Integrated Security Used in Azure Function
Azure Functions
Azure Functions is a serverless compute service that enables you to run code on-demand without having to explicitly provision or manage infrastructure.
· Integrated security — Protect HTTP-triggered functions with OAuth providers such as Azure Active Directory, Facebook, Google, Twitter, and Microsoft Account.
Azure function has function access key mechanism which provide security to access the endpoint. Function have different level of access level. Like Function, Anonymous, Admin.
General Security Flow of the Azure Function
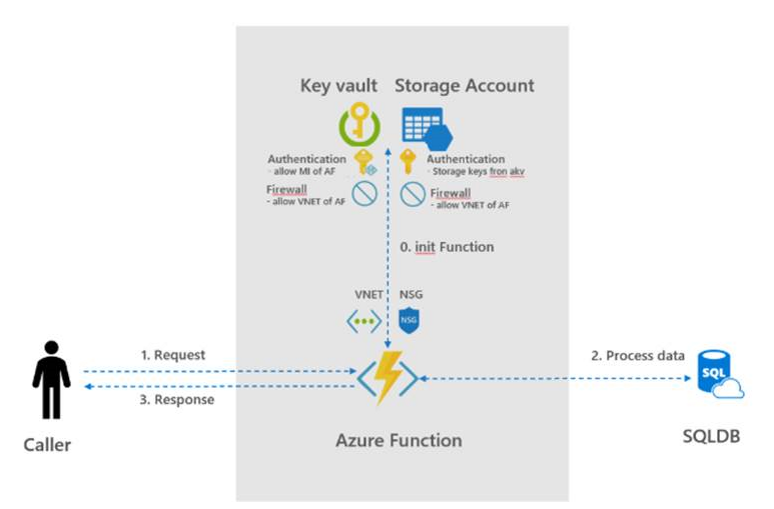
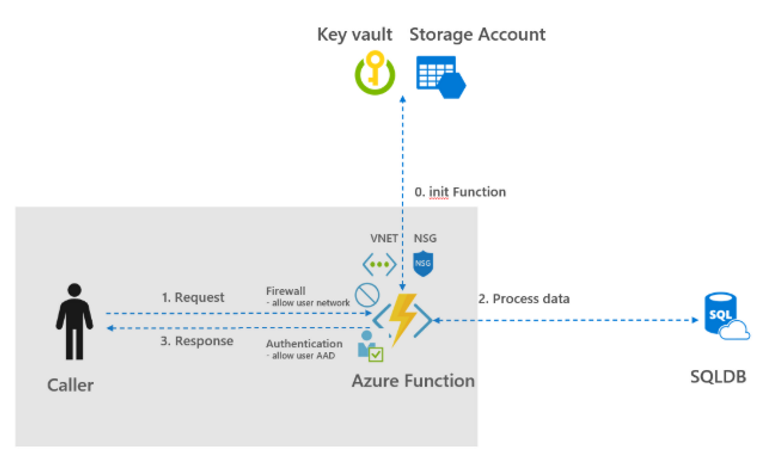
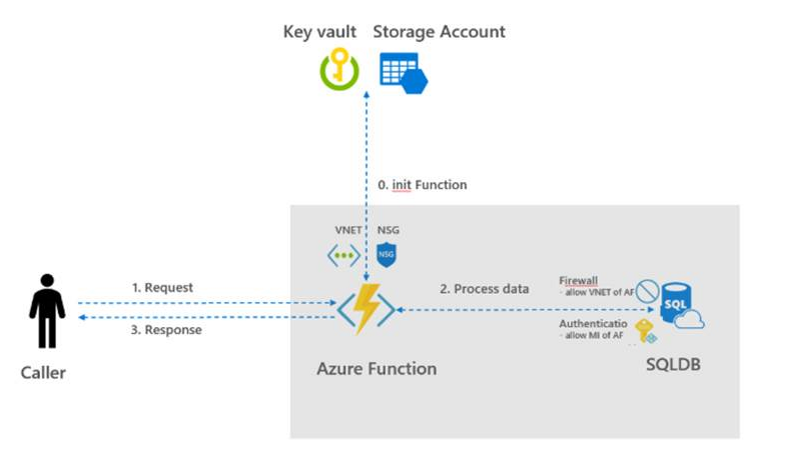
In this, Azure AD, Managed Identities, Key Vault, VNET and firewall rules are used. To create dedicated and isolated Azure Functions, it can also be decided to create a separate App Service Environment (ASE). However, an ASE can be difficult to manage and more costs are involved.
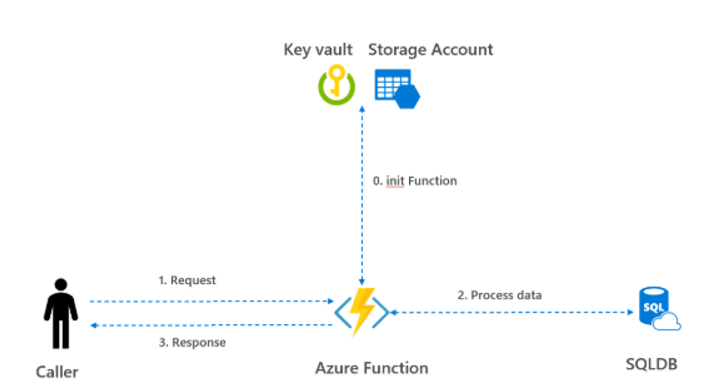
How to Secure Storage Account of Azure Function
Provide Security to Request and Response
Provide Security to Database
keys provide a default security mechanism; you may want to consider additional options to secure an HTTP endpoint in production. For example, it’s generally not a good practice to distribute shared secret in public apps. If your function is being called from a public client, you may want to consider implementing another security mechanism.
Authorization scopes (function-level)
There are two access scopes for function-level keys:
Function: These keys apply only to the specific functions under which they are defined. When used as an API key, these only allow access to that function.
Host: Keys with a host scope can be used to access all functions within the function app. When used as an API key, these allow access to any function within the function app.
Each key is named for reference, and there is a default key (named “default”) at the function and host level. Function keys take precedence over host keys. When two keys are defined with the same name, the function key is always used.
Master key (admin-level)
Each function app also has an admin-level host key named _master. In addition to providing host-level access to all functions in the app, the master key also provides administrative access to the runtime REST APIs. This key cannot be revoked. When you set an access level of admin, requests must use the master key; any other key results in access failure.
System key
Specific extensions may require a system-managed key to access webhook endpoints. System keys are designed for extension-specific function endpoints that called by internal components. For example, the Event Grid trigger requires that the subscription use a system key when calling the trigger endpoint. Durable Functions also uses system keys to call Durable Task extension APIs.
Authentication/authorization
While function keys can provide some mitigation for unwanted access, the only way to truly secure your function endpoints is by implementing positive authentication of clients accessing your functions. You can then make authorization decisions based on identity.
Enable App Service Authentication/Authorization
The App Service platform lets you use Azure Active Directory (AAD) and several third-party identity providers to authenticate clients.
Security in App Service
App service is used to secure Function app by using built in App Service features.
When you create App in default domain of the Azure like <app_name>.azurewebsites.net which is by default secure with the HTTPS in addition if you secure your app using custom domain you can also provide SSL/TLS level of security. Following are the certificates supported by App service.
Free App Service Managed Certificate
App Service certificate
Third-party certificate
Certificate imported from Azure Key Vault


