Configuring OAuth 2.0 Authentication in Power Automate
In today’s automated world, businesses depend on secure, streamlined connections between systems to improve efficiency. Power Automate, a robust tool for building workflows between various services, allows seamless integration of applications and APIs. However, when working with third-party services, ensuring that data access is secure and well-managed is critical. This is where OAuth 2.0, a secure and standard protocol for authorization, comes into play.
Are you struggling to configure OAuth 2.0 authentication in your Power Automate flows? If you are considering automating workflows that interact with secured APIs, this article is for you. I will walk you through configuring OAuth 2.0 in Power Automate, so you can ensure the safety of your automation while keeping your services accessible.
Why OAuth 2.0?
OAuth 2.0 is the industry-standard protocol for authorization. It allows users to grant third-party applications limited access to their resources without exposing passwords. By using OAuth 2.0 in Power Automate, you ensure that the services and APIs you connect to are secure, and that tokens are used to access data on behalf of the user.
How OAuth 2.0 Enhances Security
OAuth 2.0 significantly improves security by eliminating the need to share sensitive credentials. Instead, access is granted through tokens, which are time-limited and easily revocable. OAuth 2.0 is widely used by many companies, including Microsoft, Google, and Salesforce, to integrate applications securely.
Step-by-Step Guide to Configuring OAuth 2.0 in Power Automate
1. Set Up OAuth 2.0 Credentials
Before configuring OAuth 2.0 in Power Automate, you need to set up OAuth 2.0 credentials in the platform you’re working with. For example, if you’re using Microsoft Graph API or any third-party service, follow these steps:
- Register an App in Azure AD:
- a. Go to the Azure Portal and navigate to Azure Active Directory > App registrations.
- b. Click on New registration and fill in the details (name, redirect URI, etc.).
- c. After registration, note down the client ID and client secret.
- Permissions:
- a. In the API permissions section, ensure you add the necessary permissions for your app. For example, Microsoft Graph API requires permission like User.
Reador Mail.Read.
- a. In the API permissions section, ensure you add the necessary permissions for your app. For example, Microsoft Graph API requires permission like User.
2. Initialize OAuth 2.0 Variables in Power Automate
Now that you have your client ID and client secret, it’s time to configure them in Power Automate.
Set up the variables:
- Initialize Client ID:
- a. Add an “Initialize variable” action.
- b. Set the Name to
client_id, Type to String, and Value to your client ID.
- Initialize Client Secret:
- a. Add another “Initialize variable” action.
- b. Set the Name to
client_secret, Type to String, and Value to your client secret.
3. Configuring the OAuth 2.0 Connection in Power Automate
With the client credentials set, it’s time to establish the connection to the service using OAuth 2.0.
- Add the HTTP Action: In Power Automate, add an HTTP action to handle the OAuth 2.0 token request. You’ll use a POST request to authenticate using the client credentials.
- Authorization Header:
- a. In the Authorization header, use the following formula:
concat('Basic ', base64('<client_id>:<client_secret>')) - b. Replace
<client_id>and<client_secret>with the actual values from the previous step.
- a. In the Authorization header, use the following formula:
- POST Request to Token Endpoint:
- a. Set the Method to
POSTand the URI to your OAuth provider’s token URL. For example, if you’re using Microsoft Azure AD:https://login.microsoftonline.com/{tenant_id}/oauth2/v2.0/token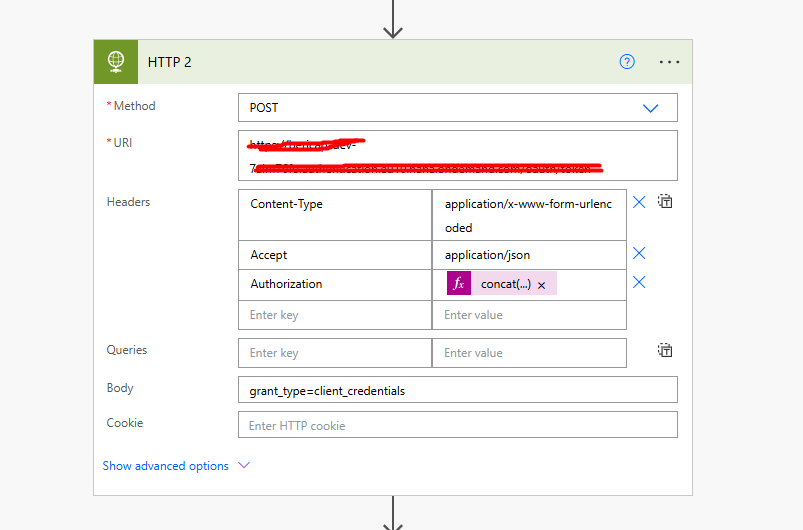
- a. Set the Method to
- Request Body:
- a. Add the necessary parameters in the Body section:
grant_type=client_credentials&scope=https://graph.microsoft.com/.default
- a. Add the necessary parameters in the Body section:
- Parse the JSON Response:
- a. After the token is successfully obtained, use a Parse JSON action to extract the
access_tokenfrom the response body. This token will be used in subsequent API calls.
- a. After the token is successfully obtained, use a Parse JSON action to extract the
4. Use OAuth Token to Access Secure Data
Now that you have the OAuth token, you can use it to authenticate your requests to third-party APIs.
- HTTP Action for API Call:
- a. Use another HTTP action to call the API. For example, you can make a request to Microsoft Graph API:
GET https://graph.microsoft.com/v1.0/me
- a. Use another HTTP action to call the API. For example, you can make a request to Microsoft Graph API:
- Authorization Header:
- a. Set the Authorization header to
Bearer {access_token}where{access_token}is the token retrieved from the previous step.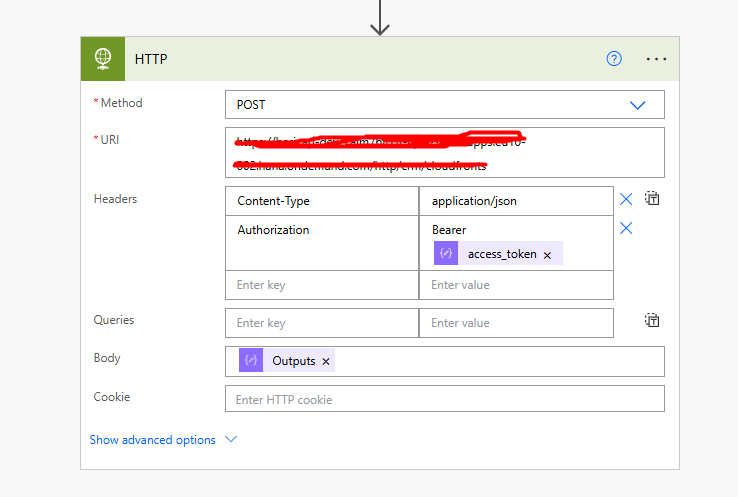
- a. Set the Authorization header to
5. Best Practices for OAuth 2.0 in Power Automate
- a. Use Azure Key Vault: Instead of storing client secrets directly in your flow, use Azure Key Vault for more secure secret management.
- b. Token Expiration: OAuth tokens have expiration times. Make sure to implement a token refresh mechanism to obtain a new token once the old one expires.
- c. Environment Variables: For more flexibility, consider using environment variables to store your client ID and client secret.
To conclude, OAuth 2.0 authentication provides a secure and effective way to authorize third-party applications in Power Automate. By following the steps outlined in this guide, you can set up OAuth 2.0 authentication, ensure data security, and integrate third-party services into your automation workflows with ease.
If you’re ready to secure your Power Automate workflows with OAuth 2.0, follow the steps outlined in this post and start integrating APIs in a secure manner today. For more tips and detailed guides, check out our other blog posts on Power Automate and API integration.
Need help with the OAuth 2.0 integration? Feel free to reach out for assistance!
We hope you found this blog useful, and if you would like to discuss anything, you can reach out to us at transform@cloudfronts.com


