Securing an API using OAuth 2.0 in Azure API Management Part 2
Part 2: Configuration of an Application (Client App) in Azure AD for Consumer
Introduction
Configuring OAuth 2.0 for your APIs hosted in Azure API Management adds an extra layer of security and prevents unauthorized access. This is a very important configuration form Security point of view for your Endpoints and is provided out of the box by Azure. This is the second part of a series of Blogs on Securing your API using OAuth 2.0 in Azure API Management. Please go through all the parts to find easy and detailed steps that will help you configure the OAuth 2.0 Authentication.
Grant permissions in Azure AD
Now that you have registered two applications to represent the API and the Developer Console, you need to grant permissions to allow the client-app to call the backend-app.
- Go to the Azure portal to grant permissions to your client application. Search for and select APP registrations.
- Choose your client app. Then in the list of pages for the app, select API permissions.
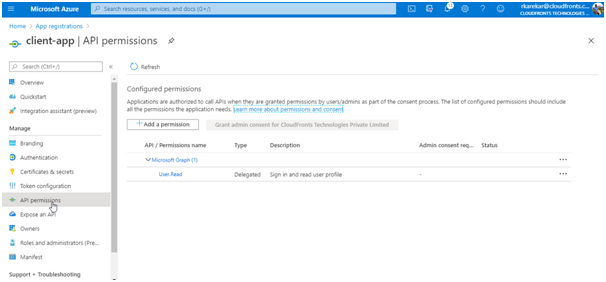
- Select Add a Permission.
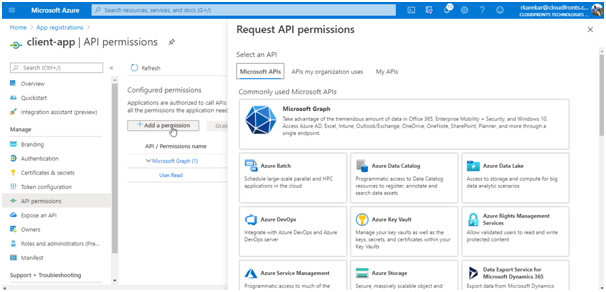
- Under Select an API, select My APIs, and then find and select your backend-app.
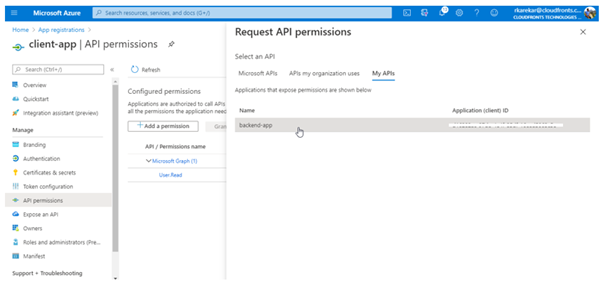
- Under Delegated Permissions, select the appropriate permissions to your backend-app, then select Add permissions.
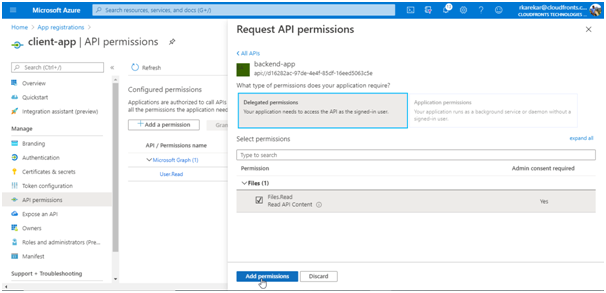
- Optionally, on the API permissions page, select Grant admin consent for <your-tenant-name> to grant consent on behalf of all users in this directory.
Part 1: Configuration of Applications in Azure AD
Part 2: Configuration of an Application (Client App) in Azure AD for Consumer
Part 3: OAUTH 2.0 Server setup
Part 4: Testing using Developer Portal and JWT Policy Configuration
